A network security assessment evaluates a computer network’s security by identifying vulnerabilities in its components and assessing their resistance to cyber threats. Professionals assess network components like firewalls, routers, switches, servers, and endpoints for their ability to resist cyberattacks and prevent unauthorized access.
Why are network security assessment important?
Network security assessments are crucial for protecting an organization’s sensitive data from cyberattacks. They help find and fix vulnerabilities that hackers could exploit. These assessments also ensure compliance with industry regulations like GDPR, HIPAA, and ISO 27001, protecting the organization’s reputation and finances.
Regular assessments serve these vital purposes:
- Assess Security Effectiveness: Gauge how well your security measures and policies work.
- Evaluate Cyber Risk: Understand the risk and potential harm of a cyberattack on your business.
- Predict Attack Likelihood: Estimate the chances of successful network attacks.
- Enhance Security: Find areas to strengthen security controls for better protection.
Apart from reducing security risks, network security assessments provide these advantages:
- Compliance Assurance: Meeting industry-specific regulations like HIPAA or PCI DSS is crucial. Assessments ensure compliance, preventing costly penalties.
- Security Awareness: Regular assessments promote security awareness among employees, encouraging best practices.
- Effective Incident Response: In case of a breach, assessment reports aid in quick and effective responses. Knowing vulnerabilities allows for timely mitigation actions.
Types of network security assessments:
Two key types of network security assessments are vulnerability assessment and penetration testing, both vital for evaluating and enhancing an organization’s cybersecurity.
- Vulnerability Assessment: This process identifies and prioritizes network weaknesses, misconfigurations, and security issues using automated tools. It helps in understanding potential entry points, prioritizing fixes, and reducing the window for cyberattacks.
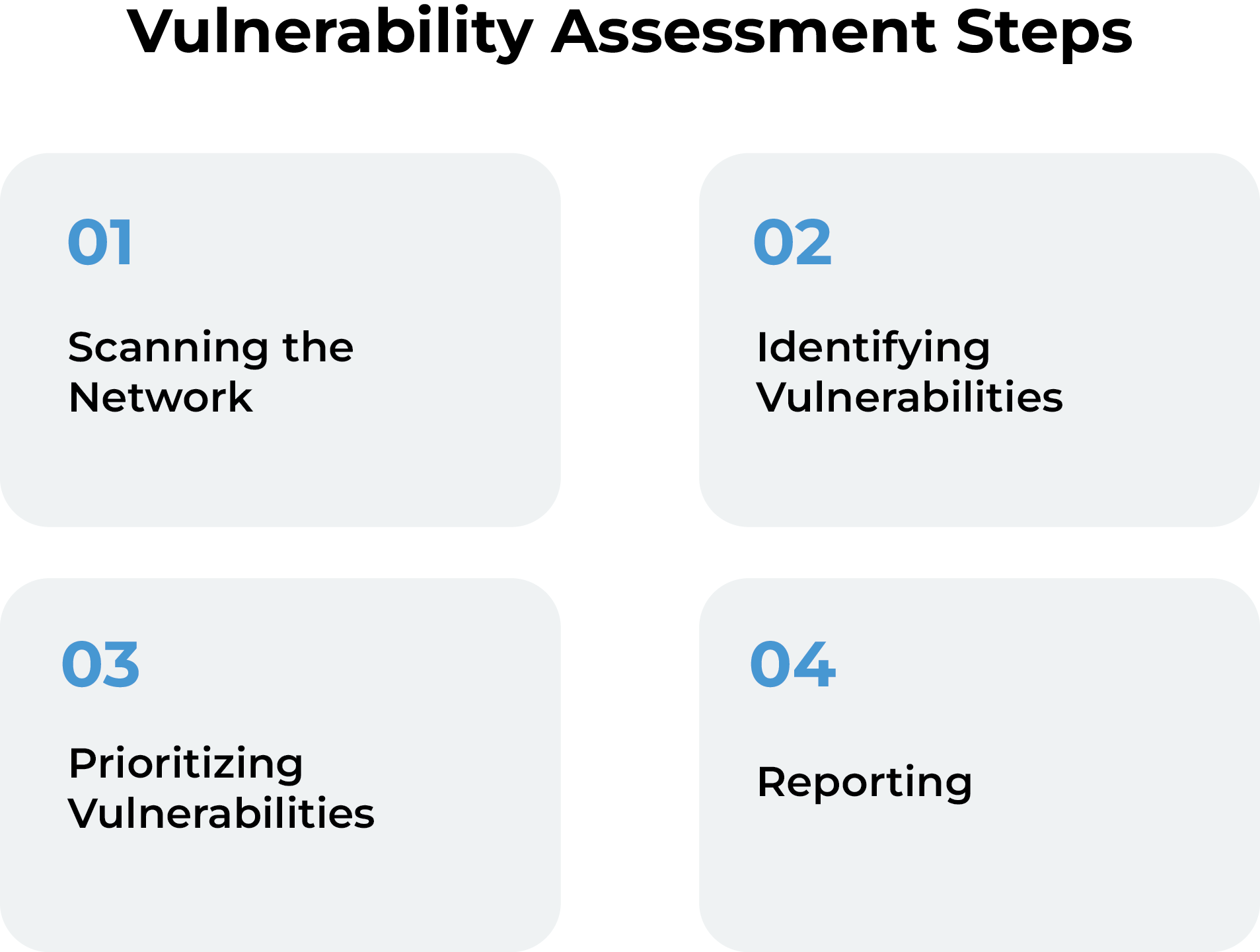
- Penetration Testing: Also known as ethical hacking, it simulates real cyberattacks to uncover hidden vulnerabilities and weaknesses. Skilled professionals manually probe systems, offering insights that automated scans might miss. This aids in fine-tuning security measures and policies.
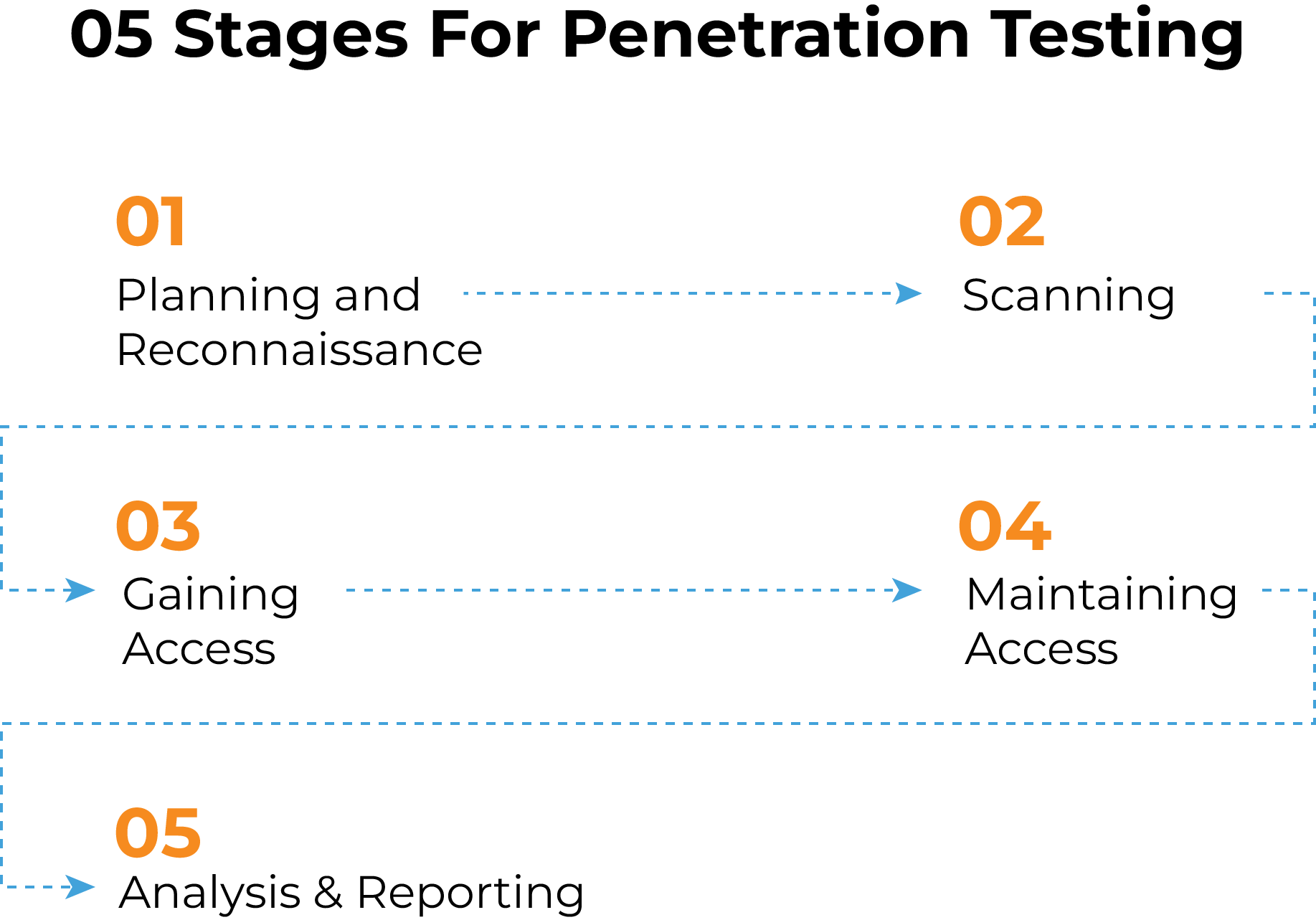
Network Security Assessment methodology:
A network security assessment follows a six-step process:
- Inventory Assets: Identify and prioritize IT resources, like networks and data.
- Find Vulnerabilities: Scan for weaknesses in both internal and external systems, databases, and policies.
- Test Security: Actively assess security controls through testing, like ethical hacking.
- Document Results: Summarize findings in reports to guide decisions.
- Plan Fixes: Turn insights into action by implementing security measures and policies.
- Monitor Continuously: Regularly watch for new threats and ensure compliance with security standards.
In short, this methodology helps organizations protect their networks and data while adhering to regulations.
More articles about Security of the system: Read More Blogs

vurcazkircazpatliycaz.yHHzC2TejzpF
vurucuteamgeldi.1PwibtJeesB3
daxktilogibigibi.ZYZOQboUc7g2
metallographist xyandanxvurulmus.GKV3HytDFkax
eski rahatiniz olmayacak vurgunyedim.BFzrKqB7szxD
anal siteleri yaralandinmieycan.zrjTLP5S0PH7
eskort siteleri citixx.4s4fycGp95VT
craft porn hyuqgzhqt.HOQqajwQXAiv
anal siteleri ewrjghsdfaa.vffDc44RvRt1
escort siteleri wrtgdfgdfgdqq.InLX8cCUZ137
craft porn wrtgdfgdfgdqq.qmpfCh2GMRFD
bahis siteleri porn sex incest wrtgdfgdfgdqq.B2qlmMuJlWQr
eskort siteleri hepxhupx.y6yCVICAzZdw
porno siteleri juljulfbi.px0fNQ5FtuyV
eski rahatiniz olmayacak bjluajszz.7yBseEOxDjcK
bahis siteleri incest category bxjluajsxzz.02f1zqOGAZVK
porn siteleri 0qbxjluaxcxjsxzz.ye4NePZzAJOA
Элвис Пресли, безусловно, один из наиболее влиятельных музыкантов в истории. Родившийся в 1935 году, он стал иконой рок-н-ролла благодаря своему харизматичному стилю и неповторимому голосу. Его лучшие песни, такие как “Can’t Help Falling in Love”, “Suspicious Minds” и “Jailhouse Rock”, стали классикой жанра и продолжают восхищать поклонников по всему миру. Пресли также известен своими выдающимися выступлениями и актёрским талантом, что сделало его легендой не только в музыке, но и в кинематографе. Его наследие остается живым и вдохновляет новые поколения артистов. Скачать музыку 2024 года и слушать онлайн бесплатно mp3.
eski rahatiniz olmayacak pokkerx.TSyjlFa0s87j
porn footballxx.PKjYSHF4IRo2
amciik siteleri mobileidn.6XGmyogy6dl9
pornhub bahis siteleri bingoxx.NjonH6yG4PSX
craft porn 250tldenemebonusuxx.xXAtMqgMcukt
bahis siteleri porn sex incest eyeconartxx.ADH1lk1y4ICo
bahis siteleri porn vvsetohimalxxvc.04djM8stwFJk
anal siteleri tthighereduhryyy.Ts6PeCOVGOM
Dating is a truly joyful experience. Sometimes we lose sight of this truth in our search for the right Online dating site
pornky com gghkyogg.OwfSPTxHY75
porn videos download hd ggjennifegg.Wkfp2AL0X8O
www porn free video ggjinnysflogg.08r0ceJeJTX
fashionflag free hd porm video fashionflag.OINOwJXLFy8
goodhere Celebrity porn vurucutewet.RploPtnk8ZA
ladyandtherose Missionary Style porn backlinkseox.HAolg5HuQcY
jenniferroy 寝取られポルノ japanesexxporns.hJJW2fGT80k
landuse Shemale porn lancdcuse.gQ4gSRupRlK
falbobrospizzamadison Shemale porn jkkıjxxx.SidJYGDbH83
शौकिया अश्लील qqyyooppxx.BZCD2kXdHdp
बड़का मुर्गा पोर्न के बा hjkvbasdfzxzz.23e7wOARrb8
लैटिन अश्लील साहित्य txechdyzxca.zBRgzTevqb7
ਕਿੰਜਰ ਪੋਰਨੋਗ੍ਰਾਫੀ madisonivysex.gTR0QkqdbJA
ladesbet ਵੱਡੇ ਗਧੇ ਪੋਰਨ ladesinemi.UOutTLPLnc0
ladesbet 輪姦ポルノ ladestinemi.2BtueTIjOr9
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Its such as you read my thoughts! You appear to know so much about this, such as you wrote the ebook in it or something. I think that you just can do with some to drive the message house a bit, however instead of that, this is wonderful blog. A fantastic read. I’ll certainly be back.
おばあちゃんポルノ .cgdcq1qAr3q
ਨੰਗਾ ਨਾਚ ਪੋਰਨ .pHdNw4hDLMz
ਹਾਰਡਕੋਰ ਪੋਰਨੋਗ੍ਰਾਫੀ .H3FUNqIrhmj
毛深いポルノ .9Dwd7r9gREj
ਲਾਤੀਨੀ ਪੋਰਨੋਗ੍ਰਾਫੀ .Uiw5qPLb5RA