As Hackers faced more complex and complicated challenges, their strategies and efforts also changing depending on the threats and the security of the system.
One of these strategies includes Advanced Persistent Threat, which is nearly impossible to detect and difficult to prevent. How can companies of all sizes keep their networks and customer data safe from advanced persistent threats (APTs)?
What is Advance Persistent Threat?
Advanced Persistent Threat (APT) are highly sophisticated and targeted cyberattacks. These are typically carried out by well-funded and organized groups, often state-sponsored, with the goal of infiltrating a specific target, such as a government agency, corporation, or organization.
APT in cyber security are known for their persistence and stealth, as they aim to remain undetected for an extended period while stealing sensitive information, disrupting operations, or conducting espionage. These attacks involve multiple stages, including initial infiltration, lateral movement within the network, and data exfiltration, making them difficult to detect and mitigate.
Rather than using broad and complex approach, APT are designed with specific target in mind. Due to this, they are developed according to the design and security of the targeted system. They first investigate and measure the security of the targeted system. They often attack by targeting the weak points or phishing links.
The main goal of Advanced persistence threat is to get access to the system rather than logging in to the system fast and furiously. This allows them to steal any type of data they want and hack the system.
One of the primary ways to advanced persistent threat to get access to the system is through network credentials. Hackers use company’s employee accounts through phishing links and get access to the system. This Helps them to remain anonymous and undetected and steal any data they want without being predicted.
Phases of advanced persistent threats:
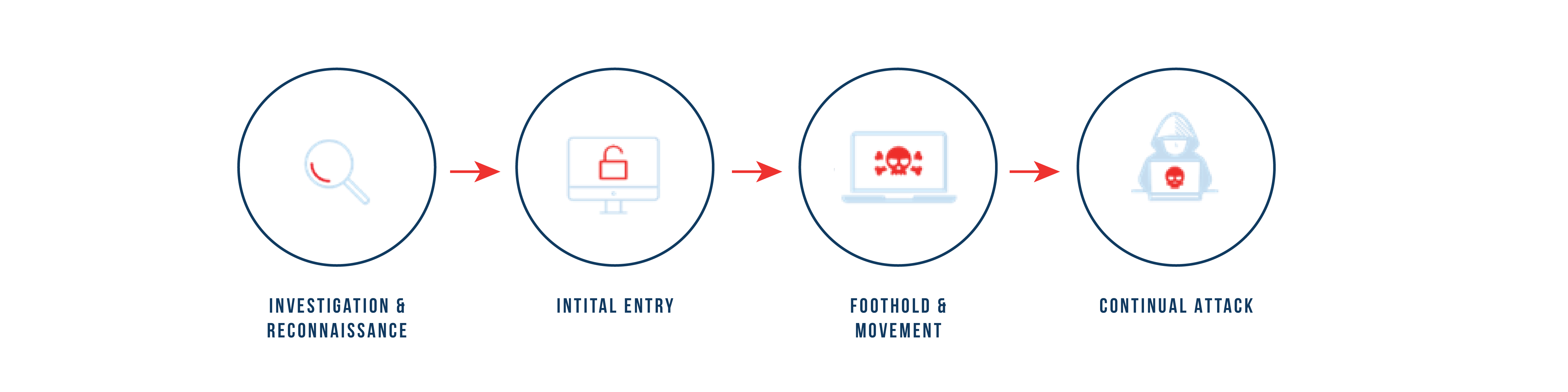
Following are the main phases of advance persistent threat:
Investigation and reconnaissance: Due to the targeted nature of these attacks, the process starts by using their resources that may be internal or external to learn about system security and the weak points that should be targeted.
Initial entry: Once the weak points originated as we discussed in the previous phase, hackers exploit them and make their initial attempt on the system.
Foothold and movement: Once they get access to the system through weak points, their main goal is to remain undetected and get strong place and hold.
Continual attack: At this point data is collected and passed back and forth from the attacker’s network. The threat will remain on the network until it is detected, which could be months or even years. The persistence of the threat is clearly seen.
How does EDR fight ATP?
Endpoint Detection and response analyze whole network and check the endpoint activity on whole network, track each activity, data flow and track behaviors for efficient workflow.
EDR (Endpoint Detection and Response) is like a cyber watchdog. It uses smart technology to watch what people do on your computer network in real-time. If it sees something weird, like too many late-night logins or big data transfers, it generates an alert so you can catch and stop the bad stuff before it stays hidden for a long time.
It is constantly monitoring your network activity so you can rest assured that anything unusual will be brought to light. It gives you the opportunity to fight back before additional damage is done.
EDR platform supports your security team by consolidating the data into reports. That reports can be analyzed by security experts—it streamlines how the alerts and attack data are managed. EDR computer security also works with your antivirus and other security tools to fight against even the most advanced attacks.
Time to challenge ATP:
Now, its time to protect your system from advance persistent threat by using endpoint detection and response tools. Acronis and Dsafe are the best EDR platform that offer best and secure platform that focuse mainly on endpoint security.
More About Acronis and DSAFE More:
Recommended Ways to Learn For Begginers : Acronis Courses

